How PCI DSS Compliance Protects Australian Businesses from Data Breaches?
VISTA InfoSec
MARCH 13, 2025
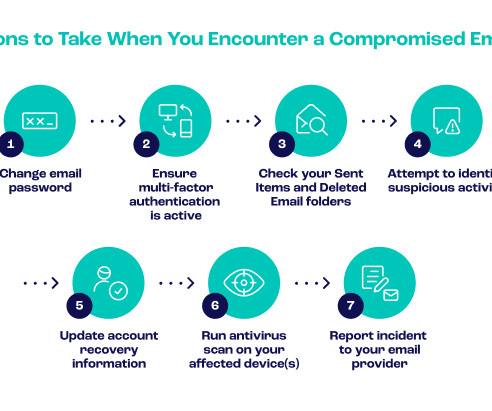
You may also check our latest YouTube video on PCI DSS 4.0 million accounts were leaked witnessing a 388% increase in compromised user accounts. Through multi-factor authentication (MFA) and role-based access controls, businesses can limit exposure to potential breaches by restricting access based on job responsibilities.
























Let's personalize your content