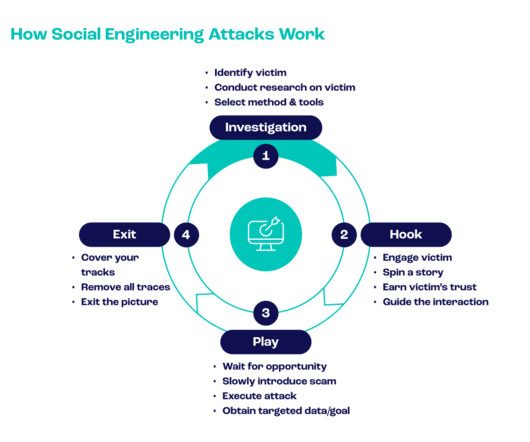
Data Breaches 101: What They Are And How To Prevent Them
VISTA InfoSec
FEBRUARY 25, 2024
Encrypt Data Flows Implement encryption for data in transit over networks and at rest within databases/servers to ensure meaningless ciphertext even if intercepted. Conduct audits periodically post-partnership.








Let's personalize your content