Build vs buy? Strategic decisions in financial crime management
The Payments Association
NOVEMBER 12, 2024
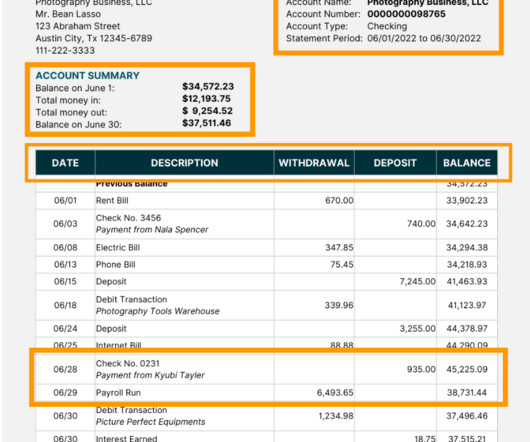
Lower Maintenance Burden: Vendor handles updates, bug fixes, and compliance changes. Vendor Dependence: Reliance on a third party for critical functions and data security. Data Privacy Concerns: Sharing sensitive data with vendors may introduce privacy and compliance risks.















Let's personalize your content