What to Know About Tokenization
Basis Theory
NOVEMBER 12, 2024
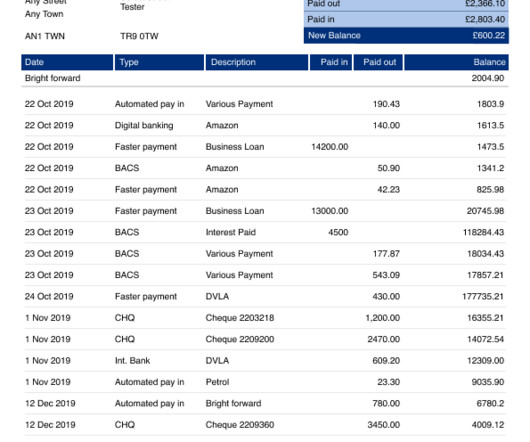
The alphabet soup of private and public data regulations, like PCI, GDPR, HIPAA, and more, endorse the use of tokenization and specialized tokenization platform providers to help organizations de-scope their compliance requirements and secure their data. The ciphertext is a computed value, based on a key and plaintext data.




































Let's personalize your content