Advanced Data Security: Safeguarding Your Business In The Digital Age
VISTA InfoSec
JUNE 18, 2024
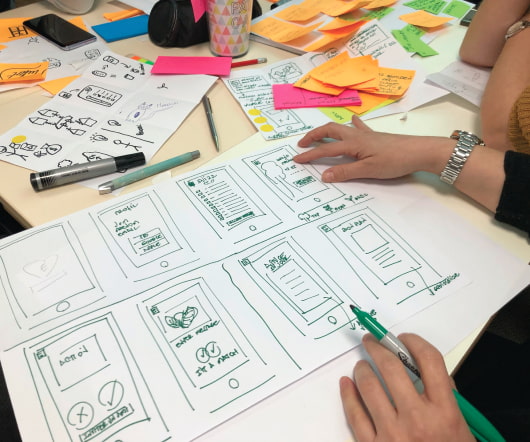
A crafty hacker could infiltrate accounts secured by flimsy credentials. This advanced data security measure demands additional verification beyond just a device passcode, such as a fingerprint scan or random code from a mobile app. A single compromised login could damage your entire network.













































Let's personalize your content