Cyber Threats Surge in India’s Financial Sector
Fintech News
MAY 8, 2025
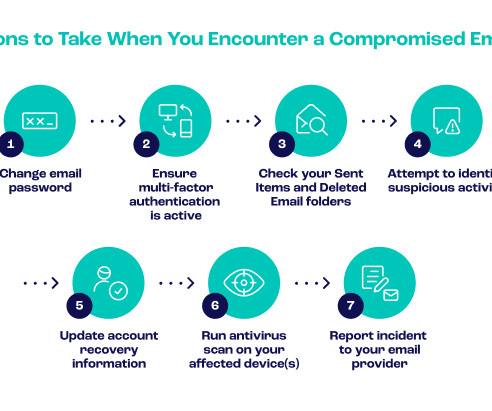
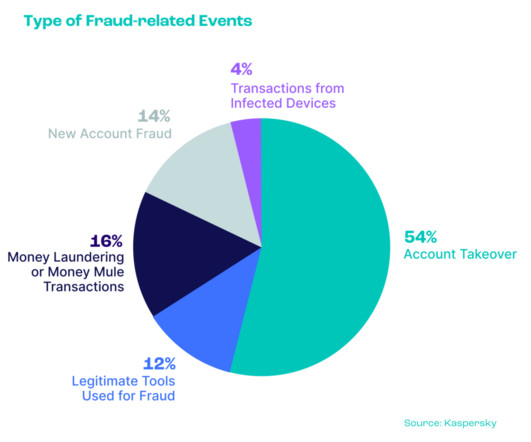
These chatbots leverage AI with natural language processing (NLP) capabilities to engage potential victims in seemingly benign conversations, subtly extracting credentials or sensitive data over time. Common vulnerabilities include poor access controls, the lack of MFA, delayed security patches, and mismanagement of privileged accounts.


































Let's personalize your content