Understanding the Nature of Payment Gateway Integration For Your Mobile App
Stax
MAY 5, 2025
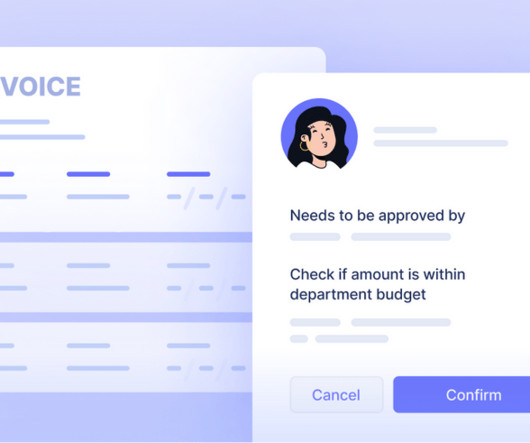
Step By Step Guide to Integrating Your Payment Gateway With Your Mobile App While the exact procedure for implementing a payment gateway for the mobile App may vary from one provider to the next, here are some general steps to keep in mind. It should also be easy for you to track conversions and manage your payments.























Let's personalize your content