Top 7 Sensible alternatives for document processing
Nanonets
NOVEMBER 19, 2024
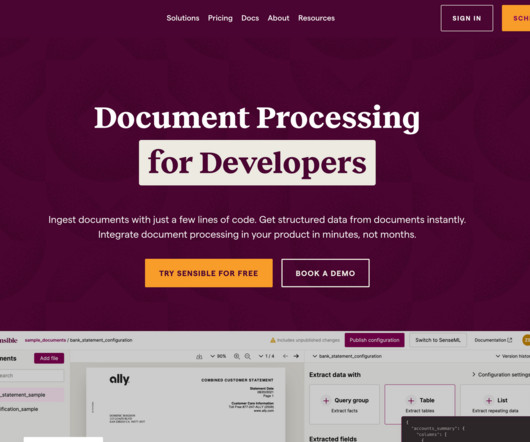
Parseur's scalable and secure solution enhances productivity by reducing manual data entry and streamlining workflows. page thereafter.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Nanonets
NOVEMBER 19, 2024
Parseur's scalable and secure solution enhances productivity by reducing manual data entry and streamlining workflows. page thereafter.

Nanonets
OCTOBER 28, 2024
for secure authentication. These are listed below: JSON payloads are lighter and faster The REST API communicates via JSON, reducing overhead compared to XML in the SOAP API. Choose the created integration and select a user and role (e.g., an admin with API permissions). Generate the Token ID and Token Secret for the application.
Nanonets
NOVEMBER 23, 2024
6 Klippa Real-time data extraction with a focus on security and GDPR compliance. Secure storage: Organizes documents in folders with unlimited storage for easy access. Role management: Assigns user roles to control access and ensure data security. Export options: Integrates with CRMs, WMS, databases, or exports as XLS/CSV/XML.
Nanonets
JANUARY 9, 2024
Introduction XML stands for Extensible Markup Language and is one of the more popular formats in which data is stored and shared between systems and software. XML is a versatile coding language similar to HTML. For most third-party applications it is easier to store, search, edit, and retrieve information from XML documents.

PYMNTS
DECEMBER 1, 2016
The move is expected to enable Visa’s global clients and partners to accelerate, scale and secure digital commerce as payments expands to include billions upon billions of connected endpoints. 3-D Secure 2.0 is an XML-based security protocol that enables consumer cards to be authenticated during card-not-present transactions.
Nanonets
SEPTEMBER 23, 2023
WebMethods Designer plays a crucial role in converting flat file data into JSON or XML. Converting flat file data into JSON or XML is a crucial step in the integration process. Converting flat file data into JSON or XML is possible using webMethods Designer.
Nanonets
JUNE 19, 2023
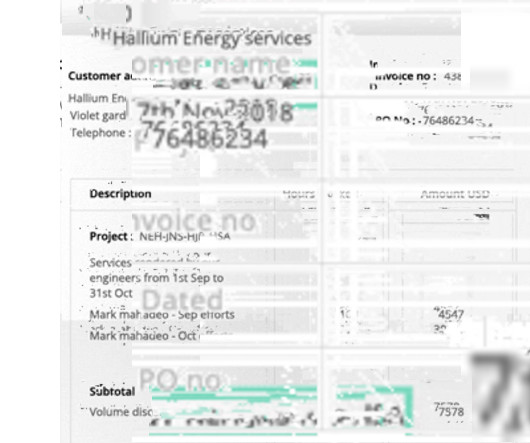
💡 While this approach can reduce data extraction costs and delays, quality control & data security are serious concerns! A super-happy Nanonets user Get Started Schedule a Demo PDF converters PDF converters are an obvious choice for those concerned about data quality & data security.
Nanonets
JUNE 19, 2023
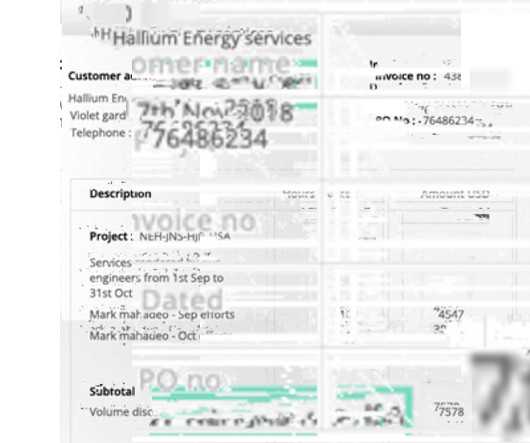
PDFTables secure & scalable table extraction API 5. Need an AI-based online OCR to convert PDF to XML or PDF to database entries , extract data from PDF , extract text from image , or extract text from PDF ? Get Started Schedule a Demo PDFTables PDFTables is a secure and scalable PDF to Excel converter and table extraction API.

Nanonets
SEPTEMBER 21, 2023
This format ensures secure and legally acceptable electronic invoicing. Dynamics 365 Finance presents itself as a reliable CFDI solution, offering businesses the capability to generate secure and legally acceptable electronic invoices. Create an invoice in the specified XML format. CFDI Process Summary 1.

Nanonets
APRIL 20, 2023
Apart from this, it is secure. The Nanonets’ image-to-text converter tool is completely free to use & requires no email registration. The JPG to Word converter also supports images like PNG, JPG, JPEG, TIFF, and more. So, it’s easy to convert JPG to Word for free.

Nanonets
JULY 29, 2024
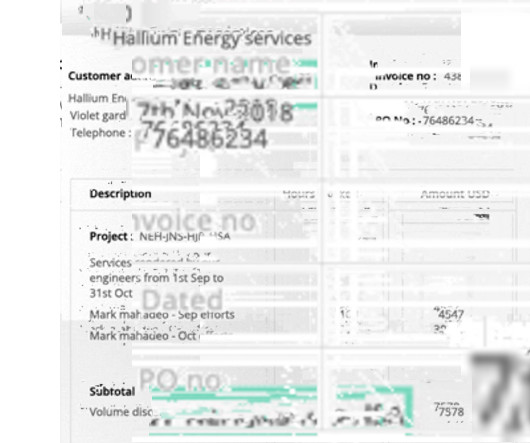
Net pay : In-hand amount after all deductions Year-to-date (YTD) totals: Total earnings and deductions for the current year Convert payslips OCR can convert payslips into PDF, TXT/Doc, CSV, XLSX, XML, or JSON formats. Data security With a surge in free OCR tools, data security is at a major risk.
Nanonets
OCTOBER 3, 2023
These tools are extremely fast, efficient, secure, and scalable. Such tools provide OCR (Optical Character Recognition) technology to recognize text from scanned documents or images within a PDF.

Nanonets
MARCH 21, 2024
Security and privacy-conscious users can examine the code to ensure no hidden data collection occurs or identify and fix vulnerabilities. JSON, XML, CSV) for further editing or integration with other systems One of Nanonets's standout features is its scalability. You can tailor them to your unique document editing requirements.

The Fintech Times
JULY 24, 2024
“RTP has also participated in cross-border initiatives like Immediate Cross-Border Payments (IXB) and built value-added services for its members – like the ability to attach PDF or XML documents to payment requests, and account number tokenisation. It’s a tough choice.

Nanonets
APRIL 18, 2023
doc), HTML XML Data PDF EDI (EDIFACT) and CSV. Data security - since most of the data read from invoices involve finance, they can be highly sensitive and the software used for automated invoice capture must be able to ensure safeguarding financial data from theft, hacking, and mismanagement.
Nanonets
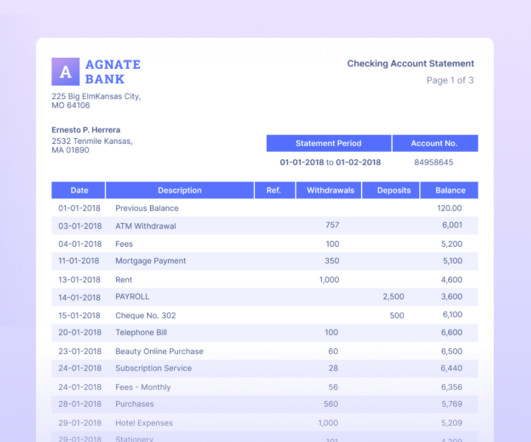
SEPTEMBER 23, 2024
They also lack robust security features, potentially exposing sensitive financial data. Customizing bank statement fields Download/export the data as different file formats (CSV, Excel, Google Sheet, XML). Manual data entry is time-consuming and prone to errors, especially as transaction volumes grow.

Nanonets
APRIL 20, 2023
Does not come with a security feature for pdf files. #7. Moreover, Wondershare PDFelement allows users to edit and save the text with a password to secure the data from piracy attacks.
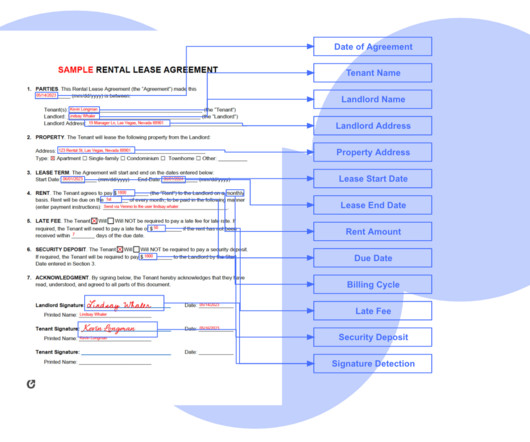
Nanonets
SEPTEMBER 25, 2024
Lease Renewal Negotiations Property management companies Lease abstraction enables managers to prepare for renewal negotiations, helping property owners secure better lease terms with current tenants. Data security: Privacy issues when using third-party LLMs for sensitive lease abstraction. Requires coding proficiency 2.
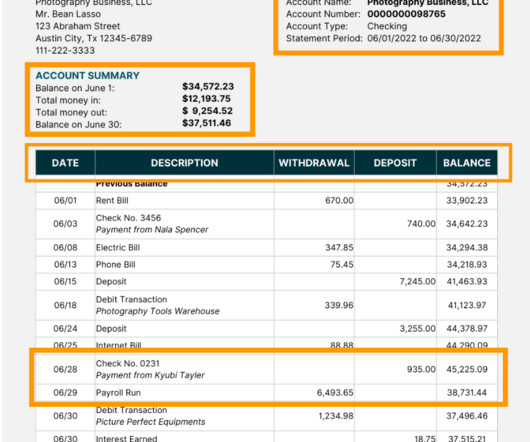
Nanonets
SEPTEMBER 25, 2024
Data security and compliance Protecting sensitive financial data should be a priority. Encryption ensures data security both when stored and when transmitted. Third-party vendor management When working with external vendors, vet their security protocols and compliance measures to ensure they meet industry standards.
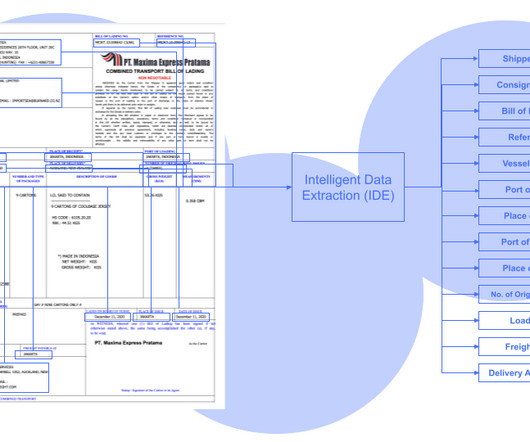
Nanonets
OCTOBER 16, 2024
Structured data output (JSON, XML, CSV, etc.) Not only can they help automate data extraction from any healthcare document, but they also come with advanced security features, like, HIPAA compliance, GDPR compliance, ISO and SoC certification, etc. Integration with existing systems (ERP, CRM, etc.)
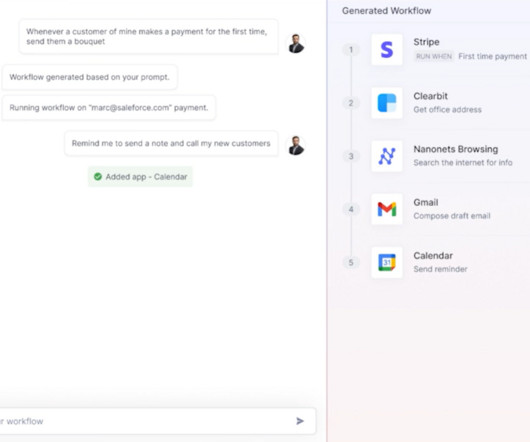
Nanonets
DECEMBER 4, 2023
Nanonets supports multiple output formats, including JSON, XML, CSV, and direct API calls to other systems. Enhance data security and compliance Automating order processing also means ensuring the data is secure and the system complies with relevant regulations. Implement robust encryption for data at rest and in transit.
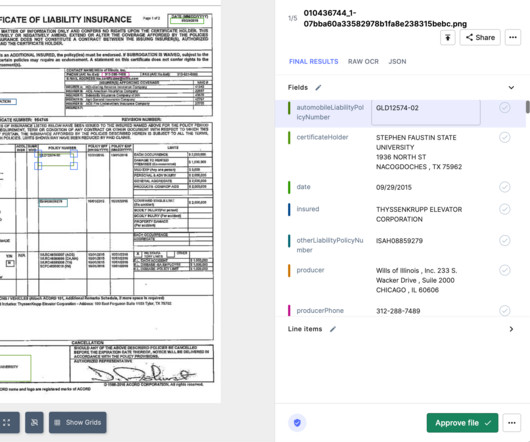
Nanonets
AUGUST 16, 2024
Automating claims processing also offers substantial benefits, such as additional cost savings, improved customer service, and strengthened data security. offers a digital check platform that allows insurers to issue payments electronically and securely.
Nanonets
AUGUST 8, 2023
Security and compliance: Ensure the software complies with relevant industry regulations and has robust security measures to protect your data. Automate data extraction and population into various formats, such as CSV, JSON, and XML, making it easy to use and analyze the data.

Nanonets
APRIL 3, 2023
Security risks : Manual form processing involves physical documents that can be lost, stolen, or damaged. OCR technology can convert physical documents into digital format, making them easier to store, manage, and secure. OCR technology can handle large volumes of forms efficiently, making it a scalable solution.

Nanonets
JANUARY 7, 2024
xls), JSON, or XML. Addressing data security concerns is also key. It creates a candidate profile by extracting information into various fields and attributes such as personal information, education, skills, experience, and many more, which are useful to recruiters. The output would be Excel (.xls),

Nanonets
JANUARY 7, 2024
xls), JSON, or XML. Addressing data security concerns is also key. Compliance Screening : Nanonets can help companies ensure compliance with regulatory requirements by identifying resumes that contain sensitive information such as social security numbers, credit card information, or other personal details.

Nanonets
MARCH 20, 2023
Accurate data capture A company may invoice invoices in various formats - paper, pdf, xml , etc. Looking to automate your manual AP Processes? It must optimise the existing setup without requiring drastic changes of existing workflows. Invoices and other financial documents may be received as mail, emails or through online forms.

Nanonets
FEBRUARY 19, 2024
Paperwork is not only costly to generate but also time-consuming to manage, expensive to retain and secure, and has a large carbon footprint. These tools can convert any scanned documents, PDFs or image types into xml , xlsx, or csv files. The industry's reliance on paperwork is a good example of this.

Nanonets
SEPTEMBER 12, 2023
Its key features include automated data extraction, real-time processing, data security measures, integration capabilities, and expense and receipts management. They can export data to Excel, CSV, JSON, and XML, integrate with Google Sheets, and access numerous other integrations.

Nanonets
MARCH 14, 2024
Managing multiple invoice formats: Large organizations handle purchase orders and invoices from various sources in diverse formats such as word documents, spreadsheets, XML documents for EDI, PDFs, images, and paper documents.

Nanonets
MAY 17, 2024
Data extraction can refer to scraping information from web pages or emails but includes any other type of text-based file such as spreadsheets (Excel), documents (Word), XML , PDFs, etc. Pricing: Free to use Best for Extracting tables from PDF Pros: High Performance Ease of Use Cons: Security Problems #9.

Nanonets
FEBRUARY 26, 2024
Audit Ready: Nanonets maintains a secure log of all activities for audit requirements. They can export data to Excel, CSV, JSON, and XML, integrate with Google Sheets, and access numerous other integrations. This flexibility allows finance professionals to address their unique document processing needs effectively.

Nanonets
APRIL 10, 2023
There may be security concerns for storing sensitive third party information on Google sheets too. Remember that the power of Google sheets are best realized when its integrated with other tools of Google ecosystem like Google forms, API, Appstore and much more. Adapt and improvise as per the need of time! Hope you enjoyed the read!

Nanonets
APRIL 16, 2023
MS-Excel files), structured XML documents from Electronic Data Interchange (EDI), PDFs and image files, and sometimes as hard copy documents. Data security and scalability: Greater operational efficiency to global businesses results from being able to run 24X7, unlike human operators who are limited by mental bandwidth and time.

Nanonets
SEPTEMBER 26, 2024
The API uses complex XML payloads and has strict formatting, so while it might initially seem nice to have a high level of detail in every API call, it can quickly become cumbersome for cases where you need to integrate the APIs at some level of scale. <soapenv:Envelope

The Payments Association
FEBRUARY 17, 2025
Unlike basic digital representations, structured formats like XML allow seamless automation, boosting efficiency and compliance. This consultation aims to establish standards for the adoption of electronic invoicing within the UK as part of a broader effort to create a digital VAT system that is more efficient and secure.
Nanonets
APRIL 7, 2025
Ensuring patient data privacy and security HIPAA compliance aside, you must ensure that every step of the extraction process, from capture to storage, adheres to strict privacy standards. Start by selecting a tool that can handle diverse formats and unstructured data, ensuring it integrates with your existing systems and prioritizes security.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content