How to Choose the Right Payment Gateway: Strategies and Tips for Payment Gateway Comparison
Stax
AUGUST 10, 2025
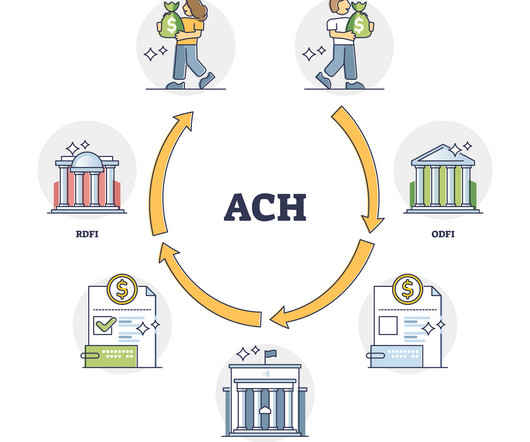
TL;DR Payment gateways securely capture and transmit customer payment data to processors, enabling businesses to accept various payment methods both online and in-store. Gateways vs. processors: Gateways handle data capture and encryption; processors move funds between banks. Some providers bundle both services.











































Let's personalize your content