Account Takeover Protection: Effective Strategies & Best Practices
Fraud.net
DECEMBER 1, 2023
Modern account takeover protection requires implementing machine learning, geolocation, and anomaly detection to spot and prevent ATO fraud.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Fraud.net
DECEMBER 1, 2023
Modern account takeover protection requires implementing machine learning, geolocation, and anomaly detection to spot and prevent ATO fraud.

FICO
MARCH 22, 2022
Account takeover fraud (ATO) occurs when an unauthorized person takes control of an account. The fraudster takes steps to actively control the account, for example by applying for a new card or changing the account contact information or password. What Do Fraudsters Do with Accounts They Have Taken Over?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Fraud.net
SEPTEMBER 23, 2024
Learn the top threats and best practices to protect your transactions and prevent fraud. Payment processing security is at risk.

PYMNTS
DECEMBER 17, 2020
Account takeovers and shipping fraud increased by 347 percent and 391 percent, respectively, between 2018 and 2019, and the pandemic has only exacerbated these issues. Digital fraud is a long-running problem for merchants, retailers, banks and businesses of all types.

Fi911
JULY 8, 2024
Furthermore, the growing sophistication of fraud techniques, including synthetic identity fraud and account takeovers, exacerbates the challenge. Merchants must combine technology, vigilance, and best practices as part of a broad, multilayered strategy.

PYMNTS
JANUARY 28, 2021
This new vigilance is the result of rampant cybertheft throughout the pandemic, from brazenly diverting government Paycheck Protection Program loans to the bad businesses of credential theft and account takeovers. Much of this is caused by criminals sensing opportunity. It’s on banks to deter them.

PYMNTS
JULY 1, 2019
Account Takeovers Plague the QSR Industry. Cybercriminals can obtain stolen identities for as little as $4, meaning it’s easier than ever for them to launch account takeover (ATO) attacks. The criminals inevitably abscond with the cash and do not follow through on their offer, resulting in damage to the restaurant’s name.

PYMNTS
NOVEMBER 16, 2016
With a nod toward the methods of the fraud attacks, Reitblat noted that fraudsters use several methods concurrently, with account takeovers, botnets and location manipulation among the most often employed conduits. and Europe.

PYMNTS
NOVEMBER 16, 2020
Fraudsters are deploying numerous methods to perpetrate this fraud, including authorized push payment (APP) schemes and account takeovers (ATOs), but these methods all have one thing in common, according to Megan Kakani , vice president of product and innovation at KeyBank. Fighting Fraud Through Technology and Education.

Fintech News
JUNE 6, 2024
This collaborative approach ensures that best practices are shared across the banking industry and that a united front is presented against the common enemy of fraud. For their part, real-time notifications should enable consumers to report any suspicious activities immediately to their FIs, facilitating timely remedial action.

FICO
OCTOBER 30, 2017
These include card-not-present fraud, such as e-commerce; other products and payment channels such as wire fraud, real-time payments, and other products and channels that are either net-new or have less sophisticated controls; different regions; and most significantly, identity-based fraud in the forms of account takeover and application fraud.

FICO
FEBRUARY 28, 2018
Instead of coding up and alerting on known patterns of how fraud operates, machine learning analytics are sensitive to the complex, multi-variate attributes that predict fraud – whether it’s payments fraud, application fraud, account takeover, mass card compromise, or more. Best Practices in Establishing Your Fraud Risk Appetite.

PYMNTS
JANUARY 23, 2020
Many of these data breaches are the result of phishing, which dupes victims into giving up login credentials or other sensitive information that is either used for account takeovers or sold on dark-web marketplaces. This comes to approximately one hack every 39 seconds, and affects a wide range of businesses and customers.

PYMNTS
FEBRUARY 27, 2020
Retail fraud attempts have doubled year over year, for example, while account takeover (ATO) fraud losses recently hit $14.7 Others, like Dropbox, are leveraging password encryption matching, and extensive employee education on best practices. billion , and phishing attacks now comprise 30 percent of all fraud attempts.
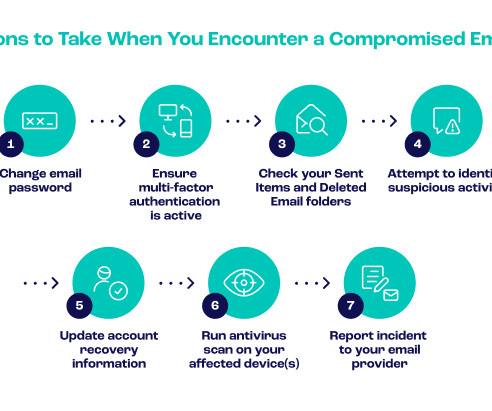
Seon
JUNE 15, 2023
A BEC attack is when a fraudster gains unauthorized access to a business’s account. The most damaging form of BEC is account takeover (ATO) attacks. Ask an Expert CEO Fraud CEO fraud is a catch-all term for the exploitation of the account of a high-ranking organizational official, such as a CEO or an investor.

PYMNTS
JULY 21, 2020
The CRI aims to create cybersecurity standards and strategies by promoting a common language for cybersecurity risk assessments, and also plans to develop a new list of cybersecurity guidelines and best practices for FIs to follow. For more on these and other financial crime news items, download this month’s Playbook.

PYMNTS
OCTOBER 26, 2018
Maeder, co-founder of the Loyalty Fraud Prevention Association , a group that offers resources, information and best practices to companies with loyalty programs, digital fraudsters have been using account takeovers (ATOs) to target these offerings. According to Peter R.

PYMNTS
MARCH 18, 2020
High-tech schemes like credential stuffing and account takeover (ATOs) have become commonplace, but many fraudsters still rely on a technique that requires comparatively little technical know-how.
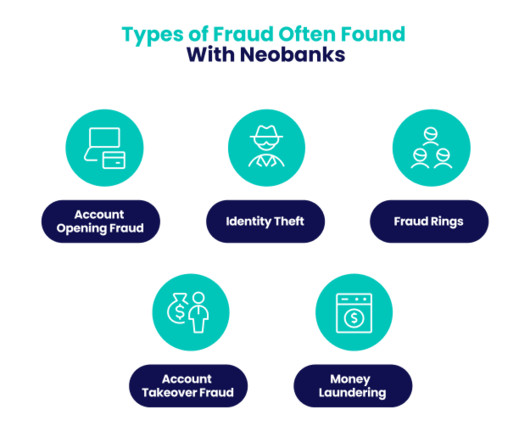
Seon
SEPTEMBER 11, 2023
As neobanks evolve, the one downside of their innovation is that it opens up many new methods of attack for fraudsters, such as identity theft, fraud rings, and account takeover attacks. Account takeover (ATO) fraud: Brute force or stolen information is used to access an existing, legitimate bank account.

PYMNTS
MARCH 30, 2016
This cloud-based, real-time identity verification tool also helps validate returning customers/prospects; it also protects transactions types, including account creation, login authentication and payment authorization. It is also used to prevent account takeover, payment fraud, identity spoofing, malware and data breaches.

FICO
DECEMBER 13, 2022
While many FIs have worked to streamline digital banking experiences, they have constantly had to add friction back into processes to prevent fraudster tactics, like SIM swaps, account takeover, and impersonation scams. However, this aversion to badly thought-out identity checks extends to use of existing accounts.

FICO
JULY 30, 2019
How FICO Is Helping Telcos See my posts on account takeover fraud, and how to tackle these kinds of fraud. Account Takeover Fraud in Telecom – 4 Things to Watch Best Practices for Fighting Subscription Fraud in the Telecom Industry

PYMNTS
JULY 12, 2019
According to the study, predicted losses due to account takeovers at call centers are set to reach $775 million by 2020. And in what is becoming a call center best practice, the virtual assistant hands the customer over to a human agent when an issue is too complex. Fraud is no small matter.

PYMNTS
SEPTEMBER 10, 2019
What we have a responsibility to do is keep things up to date and adopt the best practices for locking the bad guys out.”. So those best practices, he noted, aren’t necessarily about building the highest possible wall. Increasingly they are about finding ways to make the cleverest possible lock. Security With Simplicity

PYMNTS
FEBRUARY 22, 2019
The fallout hits everyone involved via a fraudulent transaction, and, as the data shows, account takeovers are on the rise. Establishing identity in the digital world is proving to be a fluid process, as questions are multiplying around the collection, processing and ownership of data.

FICO
JUNE 26, 2018
Key action points include: An education programme aimed at business leaders – this has already begun with a letter to CEO’s endorsing the UK Finance code of best practice. It is expected that their recommended code will be implemented by September 2018.

PYMNTS
JUNE 5, 2020
FIs monitor customers’ accounts for signs of money laundering, and FinTech partners that do the same will have an advantage in winning banks’ trust. Why AML Checks Are Never Over. FinTechs can supplement their customer data by tapping third-party repositories as well. How To Quickly Fight KYC Fraud.

Seon
JUNE 24, 2024
It prevents issues such as payment fraud, account fraud (and misuse), loan fraud, and conducting business with high-risk individuals , as well as a stipulated practice for anti-money laundering (AML) compliance. Credit card fraud accounted for 34% of these statistics, indicating fraud’s pervasive and industry-agnostic nature.

PYMNTS
APRIL 9, 2018
This could mean an employee storing sensitive company data on a personal device, or workers falling for phishing emails that lead to a data breach, business email compromise, malware or account takeovers. “To To err is human,” IBM said in its report.

PYMNTS
APRIL 30, 2019
One theory is that restaurants are new to digital technology and might not be as experienced with online security best practices as other industries. QSRs are also vulnerable to account takeovers (ATOs) where fraudsters not only steal payment information but also deplete an account of accrued points or rewards.

FICO
SEPTEMBER 14, 2021
And, if you see me at Panda Express — or at today's Aite Financial Crime Forum , where I'm participating in the feature panel, Best Practices for Operationalizing Converged Intelligence at 10:30 am ET — say hello. Leading banks worldwide use Falcon to gain a contextual, 360-degree view into customer activity. by TJ Horan.

Nanonets
MARCH 30, 2023
AP Automation solutions establish automated payment controls, including Segregation of Duties, Dual-Factor Authentication, and Positive Pay Files, which prevent internal fraud and protect against account takeovers.

Seon
JUNE 21, 2023
Like any online account, virtual credit card accounts, the mobile wallets they are kept in, and even the online bank accounts they may be connected to are vulnerable to account takeover (ATO) fraud , phishing, and more sophisticated attacks, such as man-in-the-middle attacks.

FICO
DECEMBER 19, 2022
Authenticating a customer with credentials or even biometrics at the point of entry is great, if the risk we are protecting against is Account Takeover fraud (ATO). However, if the customer themselves is being scammed, we can’t rely on that alone. See all Posts. chevron_left Blog Home. expand_less Back To Top.

Nanonets
MAY 31, 2023
Account Takeover: Criminals gain unauthorized access to customer accounts, allowing them to make fraudulent transactions or transfer funds. Stay Updated on Industry Best Practices: Keep abreast of emerging fraud trends, technologies, and regulatory changes to adapt preventive measures accordingly.

Seon
JULY 27, 2023
By keeping your resources and staff as well-equipped as possible, while also keeping yourself and your customers informed about its utilization and best practices, you will be able to help prepare your bank for FedNow. For example, real-time transaction monitoring software will be a must for your bank, given the 24/7 nature of FedNow.

The Payments Association
JANUARY 14, 2025
“Unauthorised fraud often stems from device theft,” Davey explained, noting that once criminals gain access to interconnected apps, they exploit the ecosystem to drain accounts. Fraudsters often exploit advanced social engineering tactics to deceive consumers into granting access to their accounts.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content