Economic Crime and Corporate Transparency Act examined: A guide to avoiding failure-to-prevent fraud measures
The Payments Association
FEBRUARY 10, 2025
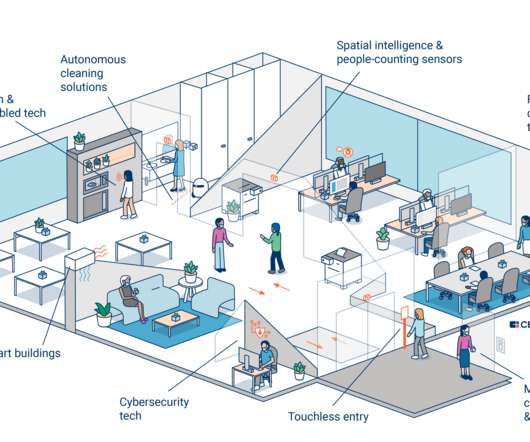
Businesses must proactively assess fraud risks, implement adequate procedures, leverage technology for fraud detection, and foster a culture of compliance to avoid regulatory penalties. Compliance requires proactive fraud risk assessment, the implementation of preventive procedures, and a culture of accountability. What’s next?








































Let's personalize your content