Chargebacks: A Survival Guide
Cardfellow
JUNE 25, 2025
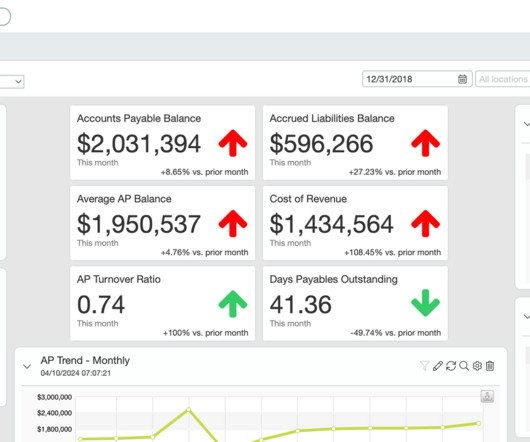
Duplicate Processing / Paid by Other Means 12.7: Duplicate Processing / Paid by Other Means 12.7: The post Chargebacks: A Survival Guide appeared first on CardFellow Credit Card Processing Blog. The individual codes are: 10.1: EMV Liability Shift Counterfeit Fraud 10.2: EMV Liability Shift Non-Counterfeit Fraud 10.3:








































Let's personalize your content